What is Nearby Devices Permission in Android? It’s a key that unlocks a world of connectivity, allowing your phone to chat with other devices nearby. Imagine your phone as a social butterfly, able to discover and interact with its peers, whether it’s your headphones, a smart speaker, or even another phone ready to share files. This permission, a relatively recent addition to the Android ecosystem, has evolved to become a cornerstone of how our devices interact with the physical world around us, and it’s a fascinating journey.
This exploration delves into the heart of the matter, unraveling the technical underpinnings, the implications for your privacy, and the best practices for developers. We’ll examine the specific APIs, the different permission levels, and the security risks, all while keeping your user experience at the forefront. We’ll also dissect the ways Android uses Bluetooth, Wi-Fi, and other methods to discover devices, comparing and contrasting the permissions required.
Get ready to understand how this permission works, how it affects you, and what the future holds for this vital piece of Android’s connectivity puzzle.
Overview of Nearby Devices Permission in Android

Alright, let’s dive into the fascinating world of the “Nearby Devices” permission on Android. This permission is all about enabling your phone to chat and connect with other devices around you, like a digital handshake for the modern age. It’s a key piece of technology that lets your phone do some pretty cool things, from sharing files to controlling smart home gadgets.
We’ll explore the basics, the types of devices involved, and how this permission has evolved over time.
Fundamental Purpose of the Nearby Devices Permission
This permission’s primary goal is to facilitate seamless communication and interaction between your Android device and other nearby devices. It’s essentially the gatekeeper that allows your phone to discover, connect, and exchange information with gadgets in its vicinity. Think of it as the facilitator of short-range wireless communication, enabling features like file sharing, device control, and location-based services. The core function is to make your phone a more connected and versatile tool.
Types of Discoverable Devices
The range of devices discoverable using the “Nearby Devices” permission is quite extensive. The permission allows Android devices to discover and interact with a variety of other devices, utilizing various communication protocols.
- Bluetooth Devices: This is perhaps the most common category, encompassing devices like Bluetooth headphones, speakers, smartwatches, and other Bluetooth-enabled gadgets.
- Wi-Fi Direct Devices: These are devices that can connect directly via Wi-Fi without needing a traditional Wi-Fi network, enabling features like file transfer between phones or printing directly to a Wi-Fi-enabled printer.
- Ultra-Wideband (UWB) Devices: With the increasing adoption of UWB technology, this includes devices that leverage UWB for precise location and secure communication, such as key fobs and smart home devices.
- Other Android Devices: Of course, it includes other Android phones and tablets, allowing for easy data transfer and interaction between them.
This permission empowers your phone to recognize and interact with a wide range of devices, transforming it into a hub for connectivity.
Android Versions and Evolution
The “Nearby Devices” permission has evolved significantly across different Android versions. Its introduction and subsequent enhancements reflect the ongoing advancements in wireless technologies and the desire for more seamless device interactions.
- Early Introductions: While the exact naming and scope have varied, the underlying functionality of discovering and connecting with nearby devices has been present for quite some time. Early versions of Android, like Android 4.3 (Jelly Bean) introduced Bluetooth Low Energy (BLE), which laid the groundwork for more efficient device discovery and communication.
- Android 6.0 (Marshmallow) and Beyond: The permission model became more refined with Android 6.0, requiring users to explicitly grant permissions for location access, which often encompassed nearby device discovery.
- Android 12 and Later: With Android 12, Google introduced more granular controls and clearer explanations for the “Nearby Devices” permission. Users gained more transparency and control over which apps could access nearby devices. The evolution of this permission is an ongoing process, with Google constantly refining the controls and improving the user experience. For instance, Android 13 introduced the ability to connect to nearby devices without needing the precise location permission, enhancing privacy and user control.
Technical Aspects of the Permission
So, you’re diving into the nitty-gritty of the Nearby Devices permission, huh? Excellent! Understanding the technical underpinnings is crucial for building apps that play nicely with Android’s security and privacy measures. It’s like knowing the secret ingredients to a delicious recipe – you can’t just wing it! Let’s get down to brass tacks and explore the tools, levels, and declarations involved.
APIs and SDKs for Accessing Nearby Devices
Developers rely on specific APIs and SDKs to interact with the Nearby Devices permission. These tools provide the building blocks for discovering and connecting with nearby devices.
- Bluetooth APIs: These are the workhorses for Bluetooth communication. The core classes, such as
BluetoothAdapter,BluetoothDevice, andBluetoothSocket, are fundamental. You useBluetoothAdapterto get the device’s Bluetooth radio,BluetoothDeviceto represent a remote device, andBluetoothSocketto establish a connection. Example:BluetoothAdapter bluetoothAdapter = BluetoothAdapter.getDefaultAdapter();This line of code gets the default Bluetooth adapter, allowing you to start discovering devices.
- Bluetooth Low Energy (BLE) APIs: BLE is optimized for low-power consumption, ideal for devices like wearables and beacons. The
BluetoothLeScannerclass is critical for scanning for BLE devices.BluetoothLeScanner scanner = bluetoothAdapter.getBluetoothLeScanner();This initializes the scanner.
- Nearby Connections API: Part of Google Play services, this API simplifies device discovery and data transfer using Wi-Fi, Bluetooth, and Ultra Wideband (UWB). It offers a higher-level abstraction, making it easier to build cross-platform experiences. The
Nearby.getConnectionsClient()method is the starting point. - Wi-Fi Direct APIs: For direct Wi-Fi connections, the
WifiP2pManagerclass and its associated APIs are used. This allows devices to create a peer-to-peer network without an intermediary access point. - Ultra Wideband (UWB) APIs: These are used to determine the relative position of the device. Android introduced support for UWB in Android 12, allowing developers to create apps that utilize this technology to provide precise positioning and directionality.
Permission Levels Associated with Nearby Devices
The Nearby Devices permission isn’t a one-size-fits-all deal. Different aspects of nearby device interaction require different permission levels, each with its own implications for user privacy and app functionality. Think of it like a set of keys, each unlocking a different door to the world of nearby devices.
BLUETOOTH_SCAN: This is required to discover Bluetooth devices. The user must grant this permission to allow your app to scan for nearby Bluetooth devices. It is considered a “nearby devices” permission and is a critical permission for any app that wants to find and connect to Bluetooth devices.BLUETOOTH_CONNECT: Necessary for establishing a Bluetooth connection. This allows your app to connect to a discovered Bluetooth device. The user also needs to grant this permission for the app to connect.ACCESS_FINE_LOCATION: Required for Bluetooth scanning on devices running Android 12 and higher. This permission is necessary because Bluetooth scanning can be used to infer the user’s location.NEARBY_WIFI_DEVICES: This permission is required to access information about nearby Wi-Fi devices. It allows the app to discover and connect to Wi-Fi devices.UWB_RANGING: This permission is required for using UWB technology. This is a special permission that grants the app the ability to measure the distance and direction of other UWB-enabled devices.
Manifest Declarations for Requesting the Nearby Devices Permission
The Android manifest is your app’s blueprint, and it’s where you declare the permissions your app needs. It’s like telling Android, “Hey, I need these keys to do my job.” Failing to declare the correct permissions will lead to your app crashing or not functioning as intended.
- Declare the Necessary Permissions:
You must declare the permissions your app needs within the
<manifest>tag of yourAndroidManifest.xmlfile. This tells the system what resources your app intends to use.Example:
<uses-permission android:name="android.permission.BLUETOOTH_SCAN" android:usesPermissionFlags="neverForLocation" />
<uses-permission android:name="android.permission.BLUETOOTH_CONNECT" />
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION" />
<uses-permission android:name="android.permission.NEARBY_WIFI_DEVICES" />
<uses-permission android:name="android.permission.UWB_RANGING" />
Note the use of
android:usesPermissionFlags="neverForLocation".This is a crucial attribute to indicate that the permission is not used for location tracking.
- Request Permissions at Runtime (for Android 6.0 and higher):
For devices running Android 6.0 (API level 23) and higher, you must request dangerous permissions at runtime. This means you ask the user for permission when your app needs it, not just during installation. This provides the user more control over their privacy.
Example (using Kotlin):
if (ContextCompat.checkSelfPermission(this, Manifest.permission.BLUETOOTH_SCAN) != PackageManager.PERMISSION_GRANTED)
ActivityCompat.requestPermissions(this, arrayOf(Manifest.permission.BLUETOOTH_SCAN), BLUETOOTH_SCAN_PERMISSION_CODE)This code checks if the
BLUETOOTH_SCANpermission has been granted. If not, it requests the permission from the user. - Handle Permission Results:
After requesting a permission, you need to handle the result in your activity’s
onRequestPermissionsResult()method. This method tells you whether the user granted or denied the permission.Example (using Kotlin):
override fun onRequestPermissionsResult(requestCode: Int, permissions: Array<String>, grantResults: IntArray)
super.onRequestPermissionsResult(requestCode, permissions, grantResults)
when (requestCode)
BLUETOOTH_SCAN_PERMISSION_CODE ->
if ((grantResults.isNotEmpty() && grantResults[0] == PackageManager.PERMISSION_GRANTED))
// Permission granted, proceed with Bluetooth scanning
else
// Permission denied, explain why the app needs the permission
else ->
// Handle other permission requests
This example demonstrates how to check if the
BLUETOOTH_SCANpermission was granted and take appropriate action.
User Privacy and Security Implications
The Nearby Devices permission, while offering exciting possibilities for connectivity and convenience, also presents significant challenges regarding user privacy and security. Understanding these implications is crucial for both developers and users to ensure responsible implementation and usage. This section delves into the potential pitfalls and provides insights into mitigating risks.
Potential Privacy Concerns
The Nearby Devices permission allows apps to discover and interact with nearby devices using various technologies like Bluetooth and Wi-Fi. This capability, while beneficial for functionalities like smart home control or file sharing, inherently raises privacy concerns related to data collection and potential tracking.
- Location Tracking: Even without direct location access, the Nearby Devices permission can be used to infer a user’s location. By detecting familiar Bluetooth devices (e.g., a home speaker) or Wi-Fi networks, an app could build a profile of a user’s frequently visited locations and movement patterns over time. This information could be used to create detailed profiles of a user’s habits and activities.
- Device Fingerprinting: The permission allows apps to gather unique identifiers of nearby devices, like Bluetooth MAC addresses or Wi-Fi network SSIDs. This information can be used to create a “device fingerprint,” a unique profile of a user’s environment and devices. Even if location data is anonymized, the device fingerprint can potentially be used to track a user across different apps and services.
- Data Leakage: Interactions with nearby devices might involve exchanging sensitive data, depending on the app’s functionality. For example, a smart home app could potentially leak data about a user’s energy consumption or home security status if not properly secured.
- Unconsented Data Collection: Apps with this permission could inadvertently collect data from other devices without the user’s explicit consent. For instance, an app could scan for and collect information from nearby Bluetooth beacons broadcasting specific data, potentially violating the privacy of individuals using those beacons.
Security Risks Compared to Other Android Permissions
The security risks associated with the Nearby Devices permission, while significant, differ in nature and potential impact compared to other Android permissions like location or camera access. The core difference lies in the potential for indirect data collection and the complexity of managing interactions with external devices.
- Indirect Data Collection: Unlike permissions like location, which directly provide a user’s geographical coordinates, Nearby Devices allows for
-indirect* data collection. An app might not know your exact location, but it can deduce it based on the devices around you. This makes it harder for users to realize what information is being collected and how it is being used. - External Device Interactions: The Nearby Devices permission involves interactions with devices outside the control of the Android operating system. This opens the door to potential security vulnerabilities in those devices, which could be exploited through the app. The risk is that if the security of a connected device is compromised, it could then potentially affect the Android device.
- Granularity of Control: The Nearby Devices permission is relatively broad. It provides access to a range of technologies and functionalities. This means that a malicious app can potentially exploit multiple attack vectors. The lack of fine-grained control for the user makes it harder to manage the risk.
- Comparison Table:
| Permission | Primary Risk | Impact |
|---|---|---|
| Location | Direct location tracking, profiling | Revealing a user’s current or past locations. |
| Camera/Microphone | Unauthorized recording, surveillance | Capturing photos/videos, recording conversations without user knowledge. |
| Contacts | Data harvesting, phishing | Stealing contact information for spam or targeted attacks. |
| Nearby Devices | Indirect location tracking, device fingerprinting, data leakage, vulnerability exploitation in external devices. | Creating detailed profiles of user behavior, potentially gaining access to sensitive data on connected devices, and enabling attacks on external devices. |
Malicious App Scenario: The “Beacon Bandit”
Imagine a malicious app called “Beacon Bandit” that masquerades as a free Wi-Fi analyzer. This app, after gaining the Nearby Devices permission, begins scanning for Bluetooth beacons. These beacons are often used by retailers to broadcast promotional offers or by transit systems to provide real-time information.
- Step 1: Data Collection: The “Beacon Bandit” identifies a user’s home Wi-Fi network SSID through the Nearby Devices permission. Then, it actively scans for Bluetooth beacons.
- Step 2: Building the Profile: The app logs the Bluetooth beacon data, correlating it with the Wi-Fi network. If a user is at home, the app detects beacons related to a nearby grocery store. This creates a profile indicating the user’s home location and shopping habits.
- Step 3: Data Exploitation: The collected data is sent to a remote server. The attackers can use this information to create targeted phishing campaigns or deliver malware based on the user’s known location and interests. The app could also identify the presence of smart home devices based on their Bluetooth signals, potentially allowing for remote control attempts.
- Step 4: Deception: To avoid detection, the “Beacon Bandit” might occasionally display generic Wi-Fi analysis results, masking its true data collection activities.
Permission Request and User Experience
The Nearby Devices permission is a critical aspect of Android app development, directly impacting user trust and the app’s functionality. Understanding the user’s journey when an app requests this permission is crucial for creating a positive and transparent experience. This section will delve into the user’s perspective, focusing on the permission request process and how developers can craft clear and informative messaging.
Process Users Go Through When an App Requests the Nearby Devices Permission
When an app needs to access nearby devices, the user will encounter a series of steps designed to ensure informed consent. This process, while seemingly straightforward, is a pivotal moment for user perception.The typical flow includes:
- Triggering the Request: The user initiates an action within the app that requires the Nearby Devices permission, such as attempting to connect to a Bluetooth device, share files via Wi-Fi Direct, or discover nearby smart home devices.
- System-Generated Dialog: Android displays a system-generated dialog box. This is the official permission request. The dialog states the app’s name, the permission being requested (Nearby Devices), and the general reason for the request. It typically provides options to “Allow” or “Deny.”
- User Decision: The user reviews the information and makes a choice: either granting the permission or denying it. This decision is crucial, as it directly impacts the app’s ability to function as intended.
- Handling the Outcome: Based on the user’s decision, the app takes action. If the permission is granted, the app proceeds to use the Nearby Devices functionality. If denied, the app should gracefully handle the situation, potentially offering alternative functionality or providing a clear explanation of why the permission is needed.
This process is designed to protect user privacy. However, the effectiveness hinges on the clarity and context provided by the app developer. A poorly worded request or a lack of explanation can lead to user confusion, distrust, and ultimately, a denial of the permission.
Examples of Clear and Concise Permission Request Messages for Users
Crafting effective permission request messages is key to user acceptance. The goal is to be transparent, informative, and concise. Here are some examples of well-written permission request messages:
- Example 1 (Bluetooth Connection): “This app needs to access nearby Bluetooth devices to connect to your headphones and play music.”
- Example 2 (Smart Home Control): “To control your smart lights, this app needs to discover and connect to devices on your local network.”
- Example 3 (File Sharing): “This app requires access to nearby devices to enable fast file sharing with other nearby phones using Wi-Fi Direct.”
Key characteristics of effective permission request messages:
- Specific Purpose: Clearly state
-what* the app will do with the permission. Avoid vague terms like “improve performance.” - Benefit to the User: Highlight the
-benefit* the user receives from granting the permission. What functionality will they gain? - Conciseness: Keep the message brief and to the point. Users are more likely to read and understand short messages.
Remember, the goal is to build trust. A well-crafted permission request message demonstrates that you value the user’s privacy and are transparent about how the app functions.
Methods for Developers to Inform Users About the Purpose of the Permission
Beyond the system dialog, developers have several avenues to educate users about the purpose of the Nearby Devices permission. This proactive approach can significantly increase the likelihood of users granting the permission and building trust.
- In-App Explanations: Provide contextual explanations within the app’s interface. For instance, before the permission request is triggered, display a brief pop-up or tooltip explaining why the permission is needed for a specific feature. This is particularly useful for features that are not immediately obvious.
- Privacy Policy and Terms of Service: Clearly Artikel the use of the Nearby Devices permission in your app’s privacy policy and terms of service. This provides a comprehensive explanation for users who want to understand how their data is handled. Make sure these documents are easily accessible within the app and on your website.
- Help and FAQ Sections: Include a dedicated help or FAQ section within the app to address common questions about the permission. This can help alleviate user concerns and provide further clarity.
- Permission Request Context Screens: Before the system dialog appears, present a custom screen that provides a more detailed explanation of why the permission is needed. This allows you to tailor the message to your app’s specific functionality.
- Use of Visual Aids: Incorporate visual aids, such as illustrations or animations, to explain the purpose of the permission. A visual representation can often be more effective than text alone, especially for complex concepts. For example, a simple animation could show how the app searches for and connects to a nearby Bluetooth speaker.
- Contextual Permission Requests: Request the permission only when the user attempts to use a feature that requires it. Avoid requesting the permission upfront without context. This approach is more user-friendly and increases the likelihood of users granting the permission.
By employing these methods, developers can foster transparency and build trust with their users. Remember that a well-informed user is more likely to grant the necessary permissions, leading to a better app experience and increased user satisfaction.
Permissions and Device Discovery Methods: What Is Nearby Devices Permission In Android
Alright, let’s dive into the nitty-gritty of how Android devices sniff out their neighbors, and what permissions are needed to make it happen. It’s like a digital game of Marco Polo, but instead of yelling, devices send out electronic signals, and sometimes, you need the right “keys” (permissions) to listen in.
Device Discovery Techniques
Android utilizes a few key methods for discovering nearby devices. These methods, each with their unique characteristics, determine how your phone or tablet connects with the world around it. Understanding these techniques is crucial to grasp the function of the Nearby Devices permission.
- Bluetooth: This is the workhorse for short-range communication. Think of it as the friendly neighbor who pops over to borrow a cup of sugar. Bluetooth Low Energy (BLE) is especially popular for device discovery because it sips power, making it ideal for things like finding fitness trackers or smart home gadgets. It works by devices advertising their presence and then establishing connections.
- Wi-Fi: Wi-Fi offers a wider range and can handle more data. It’s like having a party at your place – lots of people (devices) can connect. Wi-Fi Direct is a specific flavor of Wi-Fi designed for device-to-device communication, bypassing the need for a central router. Devices can use Wi-Fi to scan for nearby networks and other Wi-Fi Direct enabled devices.
- Ultra-Wideband (UWB): This is the new kid on the block, offering incredibly precise location and range information. UWB is like having a super-powered GPS, but for indoor environments. It’s great for things like finding your keys or unlocking your car, as it can pinpoint the location of a device with impressive accuracy. It’s also used for secure and reliable short-range communication.
Permission Requirements for Different Discovery Methods
The permissions needed for each method are not created equal. Some require more “keys” than others, reflecting the different levels of access and the potential privacy implications. Here’s a breakdown:
- Bluetooth: Generally, you need the `BLUETOOTH_SCAN` and `BLUETOOTH_CONNECT` permissions. If you are targeting Android 12 (API level 31) or higher, you must declare the `BLUETOOTH_SCAN` permission with the `usesPermissionFlags` attribute set to `neverForLocation`. This means that you don’t need location permission to scan for Bluetooth devices.
- Wi-Fi: Discovery via Wi-Fi requires the `ACCESS_FINE_LOCATION` permission in many cases, especially when scanning for Wi-Fi networks or using Wi-Fi Direct. The operating system uses this permission to determine the device’s location, which is necessary for identifying nearby Wi-Fi access points.
- Ultra-Wideband (UWB): UWB typically requires location permissions because the technology is intrinsically linked to location awareness. The exact permissions depend on the specific UWB implementation, but `ACCESS_FINE_LOCATION` or `ACCESS_COARSE_LOCATION` are usually involved.
Interaction of Nearby Devices Permission with Other Permissions
The Nearby Devices permission doesn’t exist in a vacuum; it often plays nicely (or not so nicely) with other permissions. The interaction is a critical part of the user’s experience and overall privacy.
- Location Permissions: This is where things get interesting. Historically, both Bluetooth and Wi-Fi scanning required location permissions, even if the app didn’t actually
-need* your location. This was due to the way Android’s system was designed. Now, the `BLUETOOTH_SCAN` permission can be declared without the location permission, but the app still may require it. - Runtime Permissions: Android uses a runtime permission model, meaning users are prompted to grant permissions at the time the app needs them. The Nearby Devices permission is a runtime permission, and so are the location permissions. Users have control over granting or denying these permissions, influencing how an app can discover nearby devices.
- Android’s Version Impact: The specific permission requirements and how they interact can change with each Android version. For instance, the Android 12 update brought significant changes to Bluetooth scanning and location permissions, aiming to improve user privacy.
Troubleshooting Common Issues
Dealing with the Nearby Devices permission can sometimes feel like navigating a maze. Developers often encounter various snags that can halt the device discovery process. Understanding these common pitfalls and having a solid troubleshooting strategy is key to a smooth and successful implementation. Let’s delve into the typical headaches and how to conquer them.
Device Discovery Failure Scenarios
When your app can’t find nearby devices, it can be frustrating. Let’s explore why this might happen and how to get things back on track.
- Bluetooth is Disabled: The most fundamental issue. Without Bluetooth enabled on both the discovering and discovered devices, communication is impossible. Ensure both devices have Bluetooth turned on and that the user has granted Bluetooth permissions.
- Location Services Issues: Android often requires location services to be enabled for Bluetooth scanning, even if your app doesn’t directly use location data. This is because Bluetooth beacons can sometimes be used to infer location. Double-check that location services are enabled and that the app has the necessary location permissions (ACCESS_FINE_LOCATION or ACCESS_COARSE_LOCATION, depending on the Android version).
- Permission Denials: Users might deny the Nearby Devices permission or other related permissions like Bluetooth or Location. Implement proper permission handling in your app, clearly explaining why the permissions are needed and providing options for the user to grant them later.
- Compatibility Problems: Not all Android devices support the same Bluetooth standards or features. Older devices or those with outdated Bluetooth drivers may not work seamlessly with newer protocols. Test your app on a variety of devices to identify and address any compatibility issues.
- Network Connectivity Problems: Some Nearby Devices APIs, particularly those involving Wi-Fi Direct or data transfer, may rely on network connectivity. Ensure both devices are connected to the same Wi-Fi network or that Wi-Fi Direct is properly configured.
- Hardware Limitations: Physical obstructions, such as walls or other objects, can interfere with Bluetooth or Wi-Fi signals, limiting the range and reliability of device discovery. Test in different environments to determine the optimal range for your application.
- App State and Background Restrictions: Android’s background restrictions can sometimes interfere with device discovery. Ensure your app is allowed to run in the background if necessary and that you’re handling the lifecycle events correctly.
Permission-Related Problems and Solutions
Permissions are the gatekeepers to device discovery. Getting them right is essential. Here are some common permission-related problems and how to solve them:
- Permission Not Requested: The most basic mistake. If your app doesn’t request the Nearby Devices permission, it can’t discover devices. Ensure you’re requesting the permission at the appropriate time, typically when the user initiates a device discovery action.
- Incorrect Permission Usage: Using the wrong permissions can lead to unexpected behavior. For instance, using only ACCESS_COARSE_LOCATION instead of ACCESS_FINE_LOCATION when the latter is required for certain Bluetooth scanning operations can cause issues. Carefully review the Android documentation and use the correct permissions for your specific needs.
- Permission Request Timing: Requesting permissions at the wrong time can frustrate users. Avoid requesting permissions immediately upon app launch. Instead, request them when the user tries to use a feature that requires them, such as initiating a device scan.
- Permission Denial Handling: Users may deny permissions. Your app must gracefully handle these denials. Provide clear explanations for why the permissions are needed and offer options for the user to grant them later, such as through a settings screen.
- Runtime Permission Handling: Android 6.0 (API level 23) and higher require runtime permission requests. You can’t just declare the permission in the manifest; you must also request it at runtime. Use the `ActivityCompat.requestPermissions()` method to request permissions and handle the results in the `onRequestPermissionsResult()` callback.
- Permission Revocation: Users can revoke permissions at any time through the device settings. Your app should be prepared to handle permission revocation and adapt its behavior accordingly. Regularly check if the necessary permissions are granted before attempting to use features that require them.
Alternative Approaches and Considerations
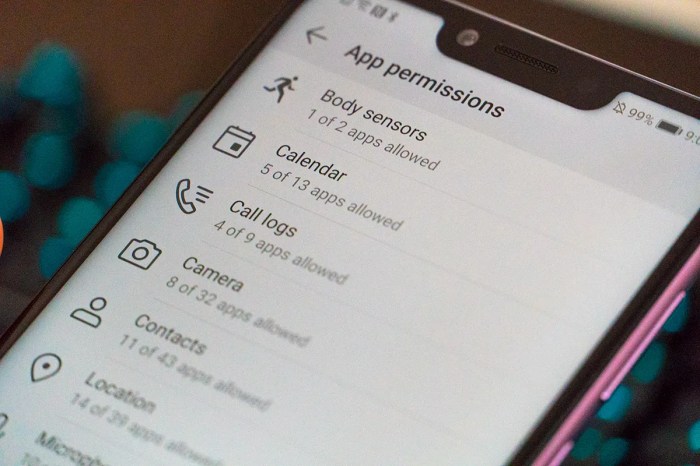
Discovering devices around us is a fundamental need in the modern digital landscape. While the Nearby Devices permission unlocks a powerful set of capabilities, it’s not the only key to this door. Several alternative methods exist, each with its own set of advantages and drawbacks. Understanding these alternatives is crucial for developers striving to balance functionality, user privacy, and system efficiency.
Let’s delve into these options and weigh their respective merits.
Bluetooth Discovery without Nearby Devices Permission
Bluetooth, the ubiquitous wireless technology, offers device discovery capabilities that don’t always necessitate the Nearby Devices permission. This is particularly relevant when interacting with specific Bluetooth profiles, such as those used for connecting to Bluetooth Low Energy (BLE) devices like wearables or smart home gadgets.Bluetooth discovery operates through a process of scanning for advertising devices. A device advertising itself sends out a signal containing its name, address, and potentially other data.
A scanning device listens for these signals and can then establish a connection if the advertising device is within range and the necessary permissions are granted (typically, Bluetooth permissions).
- Bluetooth Permissions: While you can discover Bluetooth devices without the Nearby Devices permission, you
-do* still need the appropriate Bluetooth permissions (BLUETOOTH_SCAN, BLUETOOTH_CONNECT, and, in some cases, BLUETOOTH_ADMIN). These permissions are specifically designed for Bluetooth-related operations and are more narrowly focused than the broader Nearby Devices permission. - Targeted Scanning: Developers can optimize the scanning process by specifying service UUIDs. This allows the app to focus its scan on devices advertising specific services, making the discovery process more efficient and reducing the battery drain.
- Use Cases: This approach is ideal for applications that primarily interact with known Bluetooth devices or those that use well-defined Bluetooth profiles. Think of fitness trackers, smartwatches, or devices that communicate via Bluetooth serial ports.
- Limitation: This method is limited to devices that are advertising Bluetooth services. It won’t discover devices that are not actively advertising.
Wi-Fi Direct for Device Discovery
Wi-Fi Direct enables direct, peer-to-peer Wi-Fi connections between devices, bypassing the need for a traditional Wi-Fi access point. This technology offers another avenue for device discovery, especially when high-speed data transfer is required.Wi-Fi Direct relies on a process of discovering available devices and then establishing a direct connection. This is useful for transferring files, screen sharing, and other tasks that require high bandwidth.
- No Central Access Point: Devices can communicate directly with each other, creating a temporary network. This is particularly beneficial in situations where a Wi-Fi router is unavailable or undesirable.
- High-Speed Data Transfer: Wi-Fi Direct typically offers faster data transfer rates than Bluetooth, making it suitable for transferring large files or streaming high-definition content.
- Permissions: Using Wi-Fi Direct involves permissions related to Wi-Fi functionality, such as ACCESS_WIFI_STATE and CHANGE_WIFI_STATE. These permissions are more targeted than the Nearby Devices permission.
- Use Cases: Ideal for file sharing applications, printer connections, and other scenarios that benefit from fast data transfer. For example, a file-sharing app might use Wi-Fi Direct to allow users to quickly send large files between devices without relying on a cloud service.
- Limitations: Requires both devices to support Wi-Fi Direct. It can also consume more power compared to Bluetooth.
Using QR Codes and NFC for Device Pairing
QR codes and Near Field Communication (NFC) provide simple and secure methods for initiating connections and exchanging information between devices. They don’t directly discover devices in the same way as Bluetooth or Wi-Fi Direct, but they facilitate the setup process.QR codes can encode information like Wi-Fi credentials or device identifiers. Scanning a QR code with a device’s camera can automatically configure settings or launch an app.
NFC, on the other hand, allows devices to exchange data simply by tapping them together.
- Simplified Pairing: Both technologies streamline the process of connecting devices. Users can initiate a connection with a single scan or tap, eliminating the need for manual configuration.
- Secure Information Exchange: QR codes and NFC can be used to securely exchange sensitive information, such as login credentials or payment details.
- Permissions: Using QR codes typically requires camera permission, while NFC requires NFC-related permissions. These permissions are more specific to their respective functions.
- Use Cases: Ideal for pairing devices, sharing Wi-Fi credentials, and initiating payments. For example, a restaurant could display a QR code on a table that allows customers to connect to the restaurant’s Wi-Fi network.
- Limitations: Requires physical proximity (NFC) or a camera (QR codes). Limited to exchanging relatively small amounts of data.
Comparison of Device Discovery Methods
Here’s a table comparing the various device discovery methods:
| Method | Discovery Mechanism | Permissions Required | Use Cases |
|---|---|---|---|
| Bluetooth (without Nearby Devices) | Scanning for advertising Bluetooth devices | BLUETOOTH_SCAN, BLUETOOTH_CONNECT | Connecting to Bluetooth Low Energy (BLE) devices, wearables, and smart home gadgets |
| Wi-Fi Direct | Discovering available Wi-Fi Direct devices and establishing a direct connection | ACCESS_WIFI_STATE, CHANGE_WIFI_STATE | File sharing, screen mirroring, and high-speed data transfer |
| QR Codes | Scanning a QR code containing device information | CAMERA | Simplified pairing, sharing Wi-Fi credentials, and launching apps |
| NFC | Tapping devices together to exchange data | NFC-related permissions | Pairing devices, sharing information, and initiating payments |
Future Trends and Updates
The world of Android, much like a chameleon, is constantly changing, adapting to new technologies and user needs. The Nearby Devices permission, a key player in this evolving landscape, is poised for its own transformation. Expect to see shifts in how it functions, the underlying technologies it leverages, and the overall user experience it provides. Let’s dive into the crystal ball and explore what the future holds for this important permission.
Potential Future Changes to the Nearby Devices Permission
The evolution of the Nearby Devices permission won’t be a simple upgrade; it’s more like a multifaceted project. Here’s a glimpse into the potential modifications:* Enhanced Security Protocols: Think of this as adding extra layers of armor to a knight. Future updates will likely fortify security, incorporating more robust encryption and authentication methods. This will make it even harder for malicious actors to exploit the permission for unauthorized access or data breaches.
We could see the implementation of more advanced cryptographic techniques to protect the data exchanged between devices.
Granular Control Options
Users will want even more control. Imagine being able to fine-tune exactly what devices can connect and what data they can access. The user interface might evolve to offer more granular permission settings, enabling users to customize their privacy preferences with greater precision. This might include options to allow access only to specific device types or for limited time periods.
Context-Aware Permissions
Android might become smarter. The system could learn from user behavior and offer context-aware permission prompts. For instance, if a user frequently connects to a particular Bluetooth speaker, the system might automatically suggest allowing the Nearby Devices permission when that speaker is nearby. This intelligent approach could streamline the user experience while maintaining robust security.
Integration with Emerging Technologies
The permission will likely embrace new technologies. Expect to see tighter integration with technologies like Ultra-Wideband (UWB) for even more precise device detection and spatial awareness. UWB can pinpoint a device’s location with centimeter-level accuracy, opening doors for innovative applications and enhanced user experiences.
Standardized APIs for Developers
Google might provide developers with more standardized APIs, making it easier to integrate Nearby Devices functionality into their apps. This would foster innovation, enabling developers to build more compelling and seamless experiences for users.
Improved User Interface
The user interface for managing the permission will be streamlined and more intuitive. Expect clearer explanations of what the permission does and why it’s needed, along with more straightforward controls. This focus on user education and transparency is crucial for building trust and encouraging responsible use.
Impact of Upcoming Android Releases, What is nearby devices permission in android
Each new Android release brings a wave of changes, and the Nearby Devices permission will undoubtedly feel the ripple effects.* Android Versioning and Permission Evolution: Each Android version, from the sweet treats of yesteryear to the futuristic code names of today, will bring changes. Android updates typically include enhancements to security, privacy, and user control. These releases will continue to refine the permission, making it more secure, user-friendly, and adaptable to emerging technologies.
For instance, a future release might introduce new methods for detecting and preventing rogue devices from exploiting the permission.
Enhanced Privacy Features
Google is dedicated to enhancing user privacy. Future Android versions will likely introduce new privacy features that complement the Nearby Devices permission. This could include features like Private Compute Core, which isolates sensitive data processing, or improved methods for anonymizing device identifiers. The aim is to give users more control over their data and enhance their privacy.
Performance Optimizations
Performance improvements will be a key focus. Android updates will strive to optimize the performance of the Nearby Devices permission, reducing battery drain and improving responsiveness. This will be crucial for maintaining a seamless user experience, especially with features that rely on continuous device discovery.
Developer Support and Tools
Each Android release brings new tools and resources for developers. These updates will offer enhanced APIs and SDKs for the Nearby Devices permission. These updates allow developers to build more innovative and secure applications. This will encourage the creation of new features that leverage the power of device connectivity.
How the Permission May Evolve with New Technologies
The Nearby Devices permission is not static; it’s a dynamic entity that will evolve with new technologies.* Ultra-Wideband (UWB): UWB technology is poised to revolutionize device detection.
UWB offers precise location capabilities.
Imagine being able to unlock your car door automatically as you approach, or instantly share files with a nearby friend. UWB’s ability to pinpoint device locations with centimeter-level accuracy will transform how devices interact with each other. This will require updates to the permission to handle UWB’s specific requirements, such as handling ranging data and secure key exchange.
Bluetooth 5.3 and Beyond
Bluetooth is constantly evolving. The latest Bluetooth versions introduce improvements in connection speed, range, and energy efficiency. These enhancements will lead to smoother and more reliable device discovery.
The Nearby Devices permission will need to adapt to support the new Bluetooth features.
This may involve incorporating new APIs for managing connections or optimizing the permission for low-energy scenarios.
Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML could play a significant role. Imagine a system that learns your device usage patterns and intelligently suggests appropriate permission settings. AI could also be used to detect and mitigate potential security threats, such as identifying unusual device activity.
AI could be used to enhance security and user experience.
This would involve integrating AI models into the permission framework to analyze device interactions and provide proactive recommendations.
Spatial Computing and Augmented Reality (AR)
As spatial computing and AR become more prevalent, the Nearby Devices permission will be essential for enabling seamless interactions between devices and the physical world.
Spatial computing requires precise device awareness.
This could involve using the permission to detect and interact with AR glasses or other spatial computing devices, allowing for immersive experiences. The permission would need to be updated to handle new data formats and interaction models.
Blockchain Technology
Blockchain could enhance security and privacy. Blockchain could be used to create a more secure and transparent system for managing device permissions. This could involve using blockchain to store permission settings or verify the authenticity of devices. The permission would need to be integrated with blockchain APIs to manage device access securely.
Comparison with iOS
Ah, the eternal dance of Android and iOS! When it comes to discovering nearby devices, these two mobile titans take remarkably different paths. Let’s peel back the layers and see how they stack up, focusing on their approaches to finding and interacting with the digital world around us.
Nearby Device Discovery Approaches
The methods used by Android and iOS to sniff out nearby devices differ significantly, influencing how developers build and users experience these features. These differences boil down to the core technologies they leverage and the underlying system-level design.
- Android’s Broad Spectrum: Android casts a wider net. It supports a variety of technologies, including Bluetooth Low Energy (BLE), Wi-Fi Direct, and even NFC, offering flexibility in how devices are discovered. This multi-faceted approach allows Android devices to communicate with a broader range of devices and in diverse scenarios.
- iOS’s Tight Control: iOS, on the other hand, takes a more curated approach. While it also uses BLE extensively, it often emphasizes proprietary frameworks and services like CoreBluetooth and, more recently, Nearby Interaction. This provides a more controlled and potentially more secure environment, though it can sometimes limit compatibility with non-Apple devices.
- The Bluetooth Beacon Example: Imagine a Bluetooth beacon broadcasting its signal. On Android, your app might directly scan for these beacons using the Bluetooth API. On iOS, you’d likely use CoreBluetooth or, for more sophisticated interaction, the Nearby Interaction framework, which might require additional hardware features.
Permission Model Contrast
The permission models adopted by Android and iOS reflect their philosophies regarding user privacy and system control. The way developers request and manage permissions also differs considerably, impacting the user experience.
- Android’s Granular Control: Android offers a more granular permission model. The “Nearby devices” permission is a relatively recent addition, and developers must explicitly request it to scan for and connect to nearby devices. Users have fine-grained control, often able to grant or deny permissions on a per-app basis. This can lead to a more informed user experience, but it also places a greater burden on developers to explain why they need these permissions.
- iOS’s Simplified Approach: iOS tends to bundle permissions more cohesively. While it also requires explicit permission to use Bluetooth and, by extension, discover nearby devices, the overall approach can feel more streamlined. Users are often presented with a single prompt for related permissions, simplifying the decision-making process. However, this can sometimes lead to users granting broader access than they realize.
- The Location Services Overlap: It is important to note the intersection of location services. On both platforms, scanning for nearby devices using Bluetooth or Wi-Fi can sometimes be linked to location data. This means that, in certain situations, location permissions may also be required, further complicating the permission landscape.
Developer Interaction Similarities and Differences
How developers interact with these permissions and discovery mechanisms reveals the underlying architectural differences. Understanding these differences is critical for creating cross-platform apps that work seamlessly.
- Android’s Flexibility, iOS’s Structure: Android developers enjoy greater flexibility. They have direct access to system-level APIs for Bluetooth and Wi-Fi, allowing for fine-grained control over device discovery and interaction. However, this flexibility comes with increased complexity. iOS developers, on the other hand, often work within more structured frameworks. CoreBluetooth and Nearby Interaction provide a more streamlined approach, but developers may have less control over the underlying mechanisms.
- The Permission Request Dance: Requesting permissions is a critical part of the developer workflow. On Android, developers must carefully craft permission request dialogues, explaining why they need the “Nearby devices” permission. On iOS, while the process is more straightforward, developers still need to provide clear explanations in their “usage description” strings to inform users about the app’s behavior.
- Error Handling and Edge Cases: Handling errors and edge cases is crucial. Both platforms present unique challenges. On Android, developers must account for a wider range of device models, Bluetooth versions, and operating system updates. On iOS, developers must consider the nuances of Apple’s ecosystem, including hardware limitations and the impact of background execution restrictions.
- Example: Bluetooth Scanning Differences: Consider a simple Bluetooth scanning example. On Android, you’d likely use the `BluetoothAdapter` class to start and stop scans, and you’d handle `BluetoothDevice` objects. On iOS, you’d use the `CBCentralManager` class from CoreBluetooth, and you’d work with `CBPeripheral` objects. The fundamental functionality is similar, but the APIs and the underlying concepts are different.
