How does mspy work on android – Embark on a journey into the digital world with
-how does mSpy work on android*, a fascinating exploration of a tool that offers a unique perspective on mobile device monitoring. Imagine a world where understanding the inner workings of a device is not just a technical endeavor but a narrative adventure, filled with unexpected twists and turns. This guide isn’t just about the mechanics; it’s about the story behind the technology, the choices users make, and the ethical crossroads they face.
We’ll unravel the mysteries of installation, starting with the initial steps and the granting of necessary permissions. Then, we will dive into data collection, revealing how mSpy gathers information from call logs, text messages, location data, and social media. You will discover the app’s features, from monitoring browsing history to tracking installed applications and wielding remote control capabilities. Furthermore, we’ll examine stealth mode and its impact, delving into the user interface, compatibility, device requirements, legal considerations, and troubleshooting common issues.
Each step of the way, you’ll gain a comprehensive understanding of the technology’s capabilities and its implications.
Installation Process on Android: How Does Mspy Work On Android
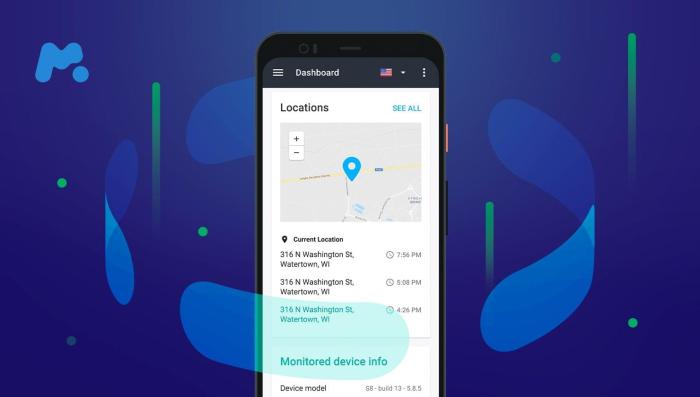
Embarking on the journey of installing mSpy on an Android device is akin to preparing for a mission – a mission of digital guardianship. This process, while straightforward, demands careful attention to detail to ensure seamless operation and discretion. Think of it as setting up a secure base camp before venturing into the digital wilderness.
Initial Steps for Installation
The initial phase involves acquiring the mSpy application file, often referred to as an APK (Android Package Kit). This file is the key to unlocking the monitoring capabilities.
- First, you will need to obtain the APK file, typically through a direct download link provided by mSpy after your subscription is activated. This link is usually sent to the email address you registered with or accessible through your online account.
- Next, on the target Android device, you must enable the installation of applications from “Unknown Sources.” This is a critical step because mSpy is not available on the Google Play Store. To do this, navigate to the device’s “Settings,” then “Security” or “Privacy,” and toggle the option to allow installations from unknown sources. This essentially grants the device permission to install apps from sources other than the official Google Play Store.
- Finally, locate the downloaded APK file (usually in the “Downloads” folder) and tap on it to begin the installation. Follow the on-screen prompts, which will guide you through the process. The prompts will generally ask you to accept the app’s permissions.
Procedure for Granting Permissions
Granting permissions is like handing over the keys to different areas of a digital home. Each permission allows mSpy to access specific features and data on the target device.
- During the installation, mSpy will request a series of permissions. These permissions are essential for the application to function correctly.
- You will be prompted to grant access to various functionalities, including contacts, call logs, SMS messages, location data, and access to the device’s storage. These permissions enable mSpy to collect and transmit the relevant information.
- Carefully review each permission request. Granting the necessary permissions is crucial for the application to function fully, but be mindful of the access you are providing.
- Some Android versions may require additional steps, such as granting “Usage Access” or “Accessibility Service” permissions. These permissions allow mSpy to monitor application usage and other activities on the device.
Hiding the mSpy Application Icon
Concealing the mSpy application icon is akin to employing a cloak of invisibility. It ensures the application operates discreetly, making it less likely to be detected by the device user.
- After the installation is complete and all permissions are granted, you will typically be given the option to hide the mSpy application icon. This is usually done during the setup process.
- Locate the option to hide the icon within the mSpy application settings. The specific wording may vary, but it will generally involve a toggle or a checkbox.
- Once you have selected the option to hide the icon, the application will disappear from the device’s app drawer and home screen. However, it will continue to run in the background, monitoring the device’s activities.
- To access the application later, you will typically need to use a secret code, a hidden URL, or a specific dial code, which you will set up during the initial configuration. Keep this access method secure and private.
Android Version Compatibility
Compatibility is the cornerstone of functionality. Ensuring mSpy functions flawlessly across various Android versions is paramount. The table below details the supported Android versions and their compatibility with mSpy. Remember that compatibility can change with updates, so it’s always wise to consult the official mSpy website for the most up-to-date information.
| Android Version | Compatibility | Key Features Supported | Notes |
|---|---|---|---|
| Android 14 | Fully Compatible | Call Monitoring, SMS Tracking, GPS Location, App Activity, Social Media Monitoring (WhatsApp, Facebook, Instagram, etc.) | Requires the latest version of mSpy. Rooting is generally not required for basic features. |
| Android 13 | Fully Compatible | Call Monitoring, SMS Tracking, GPS Location, App Activity, Social Media Monitoring (WhatsApp, Facebook, Instagram, etc.) | Rooting may be required for certain advanced features. Check the mSpy website for specific requirements. |
| Android 12 | Fully Compatible | Call Monitoring, SMS Tracking, GPS Location, App Activity, Social Media Monitoring (WhatsApp, Facebook, Instagram, etc.) | Functionality similar to Android 13, with potential for some advanced features requiring rooting. |
| Android 11 | Fully Compatible | Call Monitoring, SMS Tracking, GPS Location, App Activity, Social Media Monitoring (WhatsApp, Facebook, Instagram, etc.) | Rooting may be needed for some advanced features, especially related to accessing system-level data. |
Data Collection Methods
mSpy’s functionality hinges on its ability to gather a wealth of information from the target Android device. This data collection process is multifaceted, encompassing call logs, text messages, location data, and interactions across various social media platforms. Understanding how these collection methods function is key to grasping the software’s capabilities.
Call Log Collection
mSpy’s call log collection operates by discreetly accessing the device’s call history. This includes details such as the phone number or contact name, the duration of the call, and the date and time it occurred. The software effectively creates a detailed record of all incoming, outgoing, and missed calls.
Text Message Interception
The interception of text messages, both SMS and those from other messaging applications, is another core function. mSpy works by mirroring or duplicating the messages as they are sent and received. This gives the user access to the content of the messages, including text, images, and other attachments. The software’s capacity extends to various messaging apps, which enhances its monitoring capabilities.
Location Data Monitoring
Tracking the device’s location is achieved through the use of GPS and other location services, such as Wi-Fi positioning and cell tower triangulation. This process provides the user with real-time location data, as well as a history of the device’s movements. This feature is particularly useful for tracking the whereabouts of the device.
Social Media Data Gathering
mSpy can gather data from a range of social media platforms. The specific types of data collected vary depending on the platform but typically include:* Posts: The software captures the content of posts made by the target user.
Messages
Direct messages and chats are recorded, allowing the user to view conversations.
Shared Media
Photos and videos shared on the platform are also accessible.
User Profiles
Information from user profiles, such as names, bios, and profile pictures, is collected.This capability provides a comprehensive overview of the target user’s social media activity.
Data Types Collected from Various Apps
mSpy’s data collection extends beyond basic call logs and messages, encompassing a wide array of information from various applications. Here is a bulleted list illustrating the different data types mSpy can collect:* Messaging Apps: Text messages, media files (photos, videos), voice notes, timestamps, contact information, and group chat details from apps such as WhatsApp, Telegram, Signal, and others.
Social Media
Posts, messages, shared media (images, videos), profile information, and activity logs from platforms like Facebook, Instagram, Twitter, and TikTok.
Content of emails, including subject lines, sender and recipient details, attachments, and timestamps from email apps and webmail services.
Browser History
Visited websites, search queries, browsing history, and bookmarks from the device’s web browser.
Calendar
Calendar entries, including event details, attendees, locations, and reminders.
Contacts
Contact names, phone numbers, email addresses, and other contact information stored on the device.
Installed Apps
A list of installed applications, including app names, versions, and installation dates.
Multimedia Files
Photos, videos, and audio files stored on the device.
Keylogger Data
Records of keystrokes entered on the device, including passwords, search terms, and typed messages.
Network Activity
Data related to network connections, including Wi-Fi network names, IP addresses, and data usage.
Features and Functionality

mSpy isn’t just a simple tracking tool; it’s a comprehensive digital guardian, offering a suite of features designed to provide insights into a device’s activity. From browsing history to multimedia files, mSpy unlocks a wealth of information, offering a glimpse into the digital lives of the users you monitor. Let’s delve into the specifics of what mSpy can do.
Monitoring Internet Browsing History
Understanding online behavior is crucial in today’s digital landscape. mSpy allows you to monitor the websites visited by the user, providing a detailed browsing history.mSpy presents the browsing history in an organized format, typically including:
- Website URLs visited.
- Timestamps indicating the date and time of each visit.
- Website titles, giving context to the pages accessed.
This feature is invaluable for understanding the user’s online interests, potential risks, and overall internet usage patterns. For instance, if a user repeatedly visits websites related to specific topics, it could indicate a growing interest or even potential vulnerabilities. This information can then be used to foster discussions, offer guidance, or take appropriate action.
Tracking Installed Applications
Knowing which applications are installed on a device is vital for a complete understanding of its usage. mSpy provides detailed information about all the applications installed on the target device.This feature typically provides:
- A list of all installed applications.
- Application names and icons for easy identification.
- Installation dates and times.
- The ability to see the frequency of app usage.
This capability is particularly useful for identifying potentially harmful or inappropriate applications. It also allows you to monitor the user’s app usage patterns, helping you to understand their digital habits and preferences. Imagine the peace of mind knowing what apps your child or employee is using, and how often.
Remote Control Features
mSpy goes beyond passive monitoring, offering active control over the target device. This includes features like website and application blocking.Here’s a breakdown of the remote control capabilities:
- Website Blocking: You can block specific websites, preventing the user from accessing them.
- Application Blocking: You can block the use of certain applications.
- Device Locking: In some instances, you can remotely lock the device.
These features empower you to create a safer digital environment. For example, if a child is repeatedly visiting inappropriate websites, you can block those sites. If an employee is wasting time on social media during work hours, you can block those applications during business hours.
Accessing Multimedia Files
The ability to access multimedia files, such as photos and videos, stored on the device is another key feature of mSpy. This offers a window into the user’s visual experiences and digital interactions.mSpy typically allows you to:
- View photos and videos stored on the device.
- Download these files for safekeeping.
- View timestamps and other metadata associated with the files.
This functionality can be useful for understanding the user’s social interactions, identifying potential risks, or simply keeping track of their digital life. Think of it as a digital photo album, accessible from anywhere. For instance, you could find out if your children are sharing inappropriate content or if an employee is taking company-owned devices for personal use.
Keylogger Feature
The keylogger feature captures everything typed on the device, providing a comprehensive record of all text input. This can include messages, emails, search queries, and more.Here’s how the keylogger works:
- It records every keystroke made on the device.
- It identifies the application where the text was entered.
- It allows you to view the typed text in a chronological order.
The keylogger can be incredibly helpful in understanding the user’s communications, identifying potential threats, or simply understanding their online behavior. For example, you can see the content of their messages, search queries, and any passwords they may have typed. This information can then be used to protect them from cyberbullying, online scams, or other dangers.
mSpy’s core functionalities revolve around monitoring internet browsing, tracking installed applications, remote control, accessing multimedia, and keylogging. These features, combined, provide a comprehensive overview of a device’s activities.
Stealth Mode and User Experience
Navigating the digital world requires understanding how monitoring software operates, especially concerning its discreetness and its effect on the user experience. mSpy’s approach to stealth and its impact on device performance are critical elements in understanding its overall functionality. Let’s delve into these aspects.
Stealth Operation
mSpy is designed to operate covertly on the target device. This is achieved through several methods intended to minimize the user’s awareness of the software’s presence.
- Hiding the Application Icon: Upon installation, mSpy can be configured to hide its icon from the device’s app drawer and home screens. This prevents the user from easily identifying the application.
- Background Operation: The software runs in the background, continuously monitoring the device’s activities without requiring user interaction. This background process is optimized to consume minimal resources.
- Notifications and Alerts: mSpy is designed to avoid sending any visible notifications or alerts that could reveal its presence. This ensures the user remains unaware of the monitoring.
- Process Masking: The application’s processes are designed to blend in with other system processes, making it difficult to identify through typical device management tools.
Battery Life and Performance Impact
The operation of any monitoring software can potentially impact the target device’s battery life and overall performance. mSpy’s design considers these factors to minimize disruption.
- Resource Optimization: mSpy is engineered to use minimal processing power and memory. This is crucial for reducing battery drain.
- Background Synchronization: Data synchronization occurs in the background, utilizing efficient methods to transfer data without excessive resource consumption. The frequency of data uploads can often be adjusted to balance stealth and battery life.
- Impact on Performance: While some performance impact is inevitable, mSpy is optimized to ensure that its presence is not noticeably affecting the device’s responsiveness. The impact is typically minor and may not be perceptible to the user during regular device usage.
mSpy Control Panel User Interface
The control panel is the central hub for accessing the data collected by mSpy. The user interface is designed to be intuitive and accessible, providing a streamlined experience for reviewing information.
- Web-Based Access: The control panel is web-based, allowing users to access the data from any device with an internet connection, such as a computer, tablet, or smartphone. This provides flexibility and convenience.
- User-Friendly Design: The interface is designed with ease of use in mind, with a clean layout and clear navigation. The goal is to make the collected data easily accessible and understandable.
- Data Organization: The data is organized into various categories, such as calls, messages, location history, and social media activity. This organized structure allows users to quickly find the information they need.
Data Security Measures
Protecting the collected data is a top priority for mSpy. The company implements several security measures to ensure data confidentiality and integrity.
- Encryption: All data transmitted between the target device and the control panel is encrypted using industry-standard encryption protocols. This prevents unauthorized access to the data.
- Secure Servers: mSpy uses secure servers to store the collected data. These servers are protected with robust security measures to prevent data breaches.
- Access Controls: Access to the control panel is restricted to authorized users only. Users must log in with a unique username and password.
- Data Backup and Redundancy: Data is regularly backed up and stored redundantly to prevent data loss in the event of a system failure.
Control Panel Interface Summary
The mSpy control panel is a comprehensive interface for reviewing the collected data. The layout and data presentation are designed for clarity and ease of use.
- Dashboard Overview: The main dashboard provides a quick overview of the collected data, including recent activities and key metrics.
- Categorized Data: Data is organized into categories, such as calls, messages, location, and social media. Each category provides a detailed view of the relevant information.
- Interactive Charts and Graphs: Data is presented using interactive charts and graphs to visualize trends and patterns. For example, location data might be displayed on a map, showing the target device’s movements over time.
- Search and Filtering: The interface includes search and filtering options, allowing users to quickly find specific information. Users can search for specific s, contacts, or time periods.
- Notifications and Alerts: Users can set up custom notifications and alerts to be notified of specific activities, such as incoming calls from a specific number or location changes.
Compatibility and Device Requirements

Before you even think about tapping into the digital lives of others with mSpy, let’s talk about making sure your Android device plays nice. Compatibility is key, and understanding the specifics can save you a whole heap of trouble down the road. We’re diving into the nitty-gritty of Android versions, root access, storage space, and how it all affects mSpy’s performance.
Android Version Compatibility
mSpy isn’t a one-size-fits-all kind of deal. It’s built to work with a range of Android versions, but not every version is created equal. Understanding which versions are supported is crucial for a smooth experience.
Here’s a breakdown:
- Supported Versions: mSpy generally supports Android versions from 4.0 (Ice Cream Sandwich) up to the latest releases. However, specific feature availability can vary depending on the Android version.
- Older Versions: While mSpy may technically work on older Android versions, functionality can be limited. Features might not be as comprehensive, and updates might be less frequent.
- Newest Versions: Keeping mSpy up-to-date with the latest Android releases is a priority. This ensures compatibility and leverages new features and security enhancements.
The Root Access Conundrum
Root access is a technical term that can sound a bit intimidating, but it’s important to grasp when using mSpy. It basically means gaining administrator-level permissions on an Android device.
Here’s the lowdown:
- Rooting Requirement: Some advanced mSpy features, like monitoring specific apps or accessing deleted data, require the target device to be rooted. Think of it like needing a special key to unlock a specific door.
- Why Rooting Matters: Rooting gives mSpy deeper access to the device’s inner workings, allowing it to collect more comprehensive data.
- Rooting is Optional: Many mSpy features function perfectly fine without root access. It really depends on what you want to monitor.
The Impact of Rooting
Rooting, while powerful, isn’t without its potential downsides. It’s crucial to understand the implications before taking the plunge.
- Security Implications: Rooting can potentially weaken the device’s security. It opens the door to vulnerabilities if the user isn’t careful about what they install. Think of it like removing the locks on your front door.
- Warranty Concerns: Rooting can sometimes void the device’s warranty. Always check the manufacturer’s policy before proceeding.
- Device Stability: Incorrect rooting procedures can lead to device instability or even bricking (rendering the device unusable). Following instructions carefully is paramount.
Storage Space Demands
mSpy, like any app, needs storage space to function effectively. It’s not a huge memory hog, but it’s good to be aware of the requirements.
- Installation Size: The initial installation size of mSpy is relatively small, usually under 20MB.
- Data Storage: The amount of storage used by mSpy for data collection depends on the level of activity on the target device. Heavy usage of messaging apps, social media, and other features will increase storage needs.
- Recommendations: Ensure the target device has at least 50MB of free storage space for optimal performance. Regularly clearing cached data on the target device can also help.
Feature Compatibility Table
This table shows which mSpy features are available on different Android versions, providing a clear view of compatibility.
| Feature | Android 4.x – 5.x | Android 6.x – 9.x | Android 10.x – 12.x | Android 13+ |
|---|---|---|---|---|
| Call Monitoring | Yes | Yes | Yes | Yes |
| SMS Tracking | Yes | Yes | Yes | Yes |
| GPS Location Tracking | Yes | Yes | Yes | Yes |
| Social Media Monitoring (Rooted) | Yes | Yes | Yes | Yes |
| Social Media Monitoring (Non-Rooted) | Limited | Limited | Limited | Limited |
| Keylogger | Yes | Yes | Yes | Yes |
| Deleted Data Retrieval (Rooted) | Yes | Yes | Yes | Yes |
| App Blocking | Yes | Yes | Yes | Yes |
Legal and Ethical Considerations
The use of monitoring software like mSpy on Android devices raises a complex web of legal and ethical concerns. Navigating this landscape requires careful consideration of privacy laws, user rights, and the potential for misuse. Understanding these aspects is crucial to ensure responsible and lawful application of such technology.
Legal Implications of Using mSpy on Android Devices, How does mspy work on android
The legality of using mSpy hinges on jurisdiction and the context of its use. In many regions, monitoring a device without the owner’s explicit consent is illegal. This often falls under privacy laws that protect individuals from surveillance. These laws vary significantly; for example, some countries have stricter regulations regarding data collection and usage than others. Using mSpy to monitor a device you do not own, or without proper consent, could lead to severe consequences, including civil lawsuits and criminal charges.
Ethical Considerations Associated with Using This Type of Software
Beyond the legal boundaries, ethical considerations play a vital role. The use of mSpy involves the potential for violating an individual’s right to privacy and autonomy. Monitoring someone’s digital life, including their communications, location, and online activities, raises fundamental questions about trust and respect. It’s essential to consider the impact on the monitored individual’s relationships, mental well-being, and overall sense of security.
The potential for misuse, such as stalking or harassment, adds another layer of ethical complexity.
Guidelines on Obtaining Consent Before Monitoring a Device
Obtaining informed consent is paramount before installing and using mSpy. The consent must be freely given, informed, and specific.
“Informed consent” means the person being monitored understands what data will be collected, how it will be used, and for how long.
For example, a parent might inform their child about monitoring their phone for safety reasons, clearly outlining the data collected and its purpose. This requires open communication and transparency. In a workplace scenario, employees should be made aware of monitoring practices, including the types of data collected and the circumstances under which it will be accessed. Written consent, where possible, provides a clear record of agreement and helps avoid misunderstandings.
Detailing the Potential Consequences of Unauthorized Monitoring
Unauthorized monitoring carries significant risks. The monitored individual can file a lawsuit, leading to financial penalties and reputational damage for the user of mSpy. Furthermore, depending on the jurisdiction and the nature of the collected data, unauthorized monitoring can lead to criminal charges, including invasion of privacy or even cyberstalking. Beyond legal repercussions, there are also ethical consequences. The act of secretly monitoring someone can erode trust and damage relationships, leading to social and emotional distress for all parties involved.
Legal and Ethical Dos and Don’ts of Using mSpy
To help navigate the legal and ethical complexities, here’s a guide to what you should and shouldn’t do when using mSpy:
- Do: Obtain explicit consent from the device owner before installation. This consent should be documented, if possible.
- Do: Clearly communicate the purpose of the monitoring. Explain why the monitoring is necessary and what data will be collected.
- Do: Respect the privacy of the monitored individual. Only collect data that is necessary for the stated purpose.
- Do: Use the data responsibly. Avoid sharing the collected information with unauthorized third parties.
- Do: Adhere to all applicable privacy laws and regulations in your jurisdiction. Stay informed about any changes to these laws.
- Don’t: Monitor a device without the owner’s knowledge or consent. This is a direct violation of privacy rights.
- Don’t: Use the software for malicious purposes, such as stalking, harassment, or blackmail.
- Don’t: Collect more data than is necessary for the stated purpose. Excessive data collection can raise privacy concerns.
- Don’t: Share the collected data with unauthorized individuals or organizations. Protect the confidentiality of the information.
- Don’t: Ignore privacy laws and regulations. Failing to comply with these laws can lead to legal penalties.
Troubleshooting and Common Issues
Sometimes, even the most sophisticated technology hiccups. When dealing with mSpy, understanding how to diagnose and fix problems is crucial. This section provides a practical guide to address common issues, ensuring a smooth and effective monitoring experience. Let’s dive into some practical solutions.
Application Malfunctions
If mSpy isn’t behaving as expected, don’t panic! Here’s a structured approach to troubleshoot the application’s performance.
- Check Internet Connection: Ensure the target device has a stable internet connection (Wi-Fi or cellular data). Data transmission is essential for mSpy to function. Verify the device’s internet settings and connectivity. For example, open a web browser on the target device and try to load a website. If it fails, the internet connection is the likely culprit.
- Restart the Device: A simple restart can often resolve minor software glitches. This clears the device’s memory and can refresh the application. Power off the target device completely, wait for a few seconds, and then turn it back on.
- Verify Application Status: Check if the mSpy application is running in the background. Some devices have task managers where you can view running applications. If mSpy isn’t listed, it might have crashed or been closed.
- Reinstall the Application: As a last resort, reinstalling mSpy can fix corrupted files or configuration issues. Uninstall the application from the target device and then reinstall it following the original installation steps.
- Contact Support: If the problem persists, contact mSpy’s customer support. Provide detailed information about the issue, including error messages, device model, and operating system version. Their expertise can help resolve complex problems.
Data Synchronization Issues
Data synchronization is the backbone of mSpy’s functionality. When data doesn’t update, it can be frustrating. Here’s how to get things back on track.
- Check Internet Connectivity: As previously mentioned, a reliable internet connection is crucial for data synchronization. Ensure the device is connected to the internet.
- Verify mSpy Application Status: Ensure the mSpy application is running and has permission to access the internet. Some devices have data usage restrictions that could prevent the application from synchronizing data.
- Check the Control Panel: Log into your mSpy control panel to see the last data update. This helps determine if the issue is with the device or the account.
- Restart the Application: Restarting the mSpy application on the target device can sometimes initiate a new synchronization process.
- Check Device Storage: If the target device’s storage is full, it may hinder the application’s ability to store and send data. Clear some space on the device by deleting unnecessary files or applications.
- Update the Application: Make sure you have the latest version of mSpy installed. Updates often include bug fixes and performance improvements that can resolve synchronization problems.
Battery Drain Problems
Excessive battery drain is a common concern. Here’s how to address potential battery drain issues associated with mSpy.
- Optimize Settings: Review the application’s settings on the target device. Some features, like excessive location tracking frequency, can consume more battery. Adjust the settings to find a balance between monitoring and battery life.
- Check Application Updates: Ensure the mSpy application is up to date. Newer versions often include optimizations that reduce battery consumption.
- Monitor Application Usage: Use the device’s battery usage monitor to see how much power mSpy is using. This can help identify if the application is the primary cause of the battery drain.
- Reduce Monitoring Frequency: If the device’s battery life is significantly affected, consider reducing the frequency of data updates or location tracking.
- Device Compatibility: Confirm the device meets the minimum system requirements for mSpy. Older or underpowered devices may struggle to run the application efficiently, leading to faster battery drain.
Installation Problems
Installation errors can occur, but they are often solvable. Here’s how to tackle common problems during installation.
- Check Compatibility: Verify that the target device is compatible with mSpy. The application’s website provides a list of supported devices and operating system versions.
- Ensure Sufficient Storage: Make sure the target device has enough free storage space to install the application.
- Disable Security Software: Temporarily disable any security software (antivirus, etc.) on the target device, as it might interfere with the installation process. Remember to re-enable it after installation.
- Follow Installation Instructions: Carefully follow the installation instructions provided by mSpy. Any deviation can lead to errors.
- Check Internet Connection: Ensure the target device has a stable internet connection during installation.
Troubleshooting Installation Errors:
- Error Message: “Installation failed” or similar.
- Solution: Double-check compatibility, free up storage space, disable security software, and ensure a stable internet connection.
- Error Message: “Application not installed.”
- Solution: Verify the installation file, check for conflicts with other applications, and ensure sufficient device permissions.
- Error Message: “Parse error.”
- Solution: Download the installation file again, as it might be corrupted.
